CGHMN Certificate Authority
The CGHMN Certificate Authority
... is used to create internal certificates for old SSL and TLS applications with our custom domains .cghmn and .retro, which cannot receive actual, real world publicly trusted certificates.
To trust those certificates, navigate to http://certs.cghmn, download the Root CA certificate and install it into your operating systems root CA store.
WARNING: Only do this on retro machines that are attached to the CGHMN, don't do this on modern machines with data you care for and websites you'd rather not have potentially MITM'ed. Installing and trustig the Root CA certificate would allow us (or anyone that has access to the root CA public and private keys together with the signing password) to create whatever certificate we like for any domain name out there and fool your OS into thinking it can trust that self-signed certificate.
Alternatively, you can always just click "Trust this page" or similar in your web browser and most applications that rely on SSL/TLS have some option to disable CA checking.
How to obtain a certificate for your .cghmn or .retro domain
If you'd like a certificate for your CGHMN internal domain, ping one of the admins in the Discord channel and pass along the following infos:
- Domain Name: The domain you'd like to receive a certificate for
- How to best send you your certificate, e.g. Discord DMs, E-Mail, some Messenger, Filesharing service etc., best not through a public channel
- Optionally:
- If you want a wildcard certificate, i.e. one certificate for the domain above and all subdomains underneath that domain (e.g. *.example.org)
- If you'd like the private key to be protected with a randomly generated password
- What two letter code to fill into the "Country" field of the certificate, default is "XX"
- What to fill into the "State or Province" field of the certificate, default is "Global"
- What to fill into the "Locality" field of the certificate, defaut is "The Internet"
- What to fill into the "Organization Name" field of the certificate, default is "Compu Global Hyper Mega Network"
- What to fill into the "Organizational Unit" field of the certificate, default is your username
- What to fill into the "E-Mail" field of the certificate, default is "complain@mail.cghmn"
- All of the above can be freely chosen and be whatever you like
Then we'll create the certificate, private key and full chain certificate and send it over so you can install it into whatever service you like!
How to generate a certificate - For CGHMN Admins
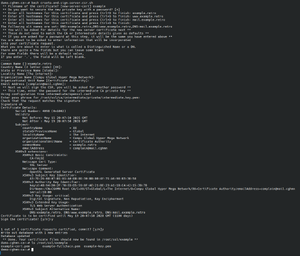
To generate a members' certificate, ssh or pct enter into Container 11013 with IP address 100.64.11.13. In the root directory should be a Bash script called create-and-sign-server-csr.sh, run it with bash /root/create-and-sign-server-csr.sh.
It will first ask you what the output files should be called, it's best to enter something that associates the file with the target domain or member, e.g. the domain itself or the members' username. It's recommended to only use alpha-numerical characters, dashes, underscores and dots.
Next, you're asked if the key shall be protected with a password. If the member didn't specify or doesn't want one, you can just press Enter on this step to select the default value of not using a password. Otherwise type y and press Enter to confirm, then generate a random password with a website, tool or password manager of your choice and input said password in the "Enter PEM pass phrase" prompt. The password needs to be at least 4 characters long!
The next step asks you for the hostnames of the certificate. Enter all hostnames you want the certificate to be valid for, e.g. example.retro, www.example.retro and mail.example.retro. If the member requested a wildcard certificate, enter the base domain first, e.g. example.retro, followed by the wildcard domain, e.g. *.example.retro. Once all domain names are entered, press Ctrl+D to confirm.
If you've specified y at the question above if the private key should be password protected, you will next be asked to re-enter that password.
Next, you'll be asked for the Common Name, there enter the base domain for which the certificate is valid, e.g. example.retro.
Then, some certificate options can be set like Country, Organization and E-Mail assigned with the certificate, which are most of the optional details listed above that the member can specify if they like, which does not need to be real data, it can be whatever they like. Otherwise, just press Enter on the fields to select the predefined default values.
The next password requested from you is the Intermediate CA Signing Password, followed by two confirmations if you really really want to sign the new certificates with our intermediate CA. Input y and press Enter both times.
Now the certificate is created and ready for use, the script will tell you into which directory it has written the certificate files.
All that's left to do now is to SCP the files off the CA container and send them over to the member in a secure-ish fashion through their prefered channel. Don't send them in the Discord channel unless they're fine with it since it allows someone else to more easily impersonate their site, not that that's a huge concern in the CGHMN network, but still.