How to Get Connected: Difference between revisions
m Added a link to user admin side tutorial |
m OPEN beta! |
||
| (8 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Compu-Global-Hyper-Mega-Net]] | |||
This is a quick and dirty "how do I get on CGHMN" | This is a quick and dirty "how do I get on CGHMN" | ||
'''Since the service is in "open beta" these steps are a bit vague and manual. But over time as we figure out what works we'll add more connection methods and better documentation''' | |||
=== Step 1: === | |||
[[Signup|'''Let us know you'd like to connect!''']] | |||
(We'll need information from you such as your Wireguard Pubkey to let you connect to the network)[[File:CGHMN.png|thumb|319x319px|Example CGHMN Router Setup using a GL-AR300M and basic network switch]] | |||
[[File:CGHMN.png|thumb|319x319px|Example CGHMN Router Setup using a GL-AR300M and basic network switch]] | |||
=== Hardware requirements === | === Hardware requirements === | ||
| Line 23: | Line 24: | ||
# Update your OpenWRT install to the latest version to ensure all required packages are available and compatible. | # Update your OpenWRT install to the latest version to ensure all required packages are available and compatible. | ||
# Download [https://raw.githubusercontent.com/jonasluehrig/cghmn-get-connected/refs/heads/main/openwrt/setup-cghmn.sh this script from GitHub] to your OpenWRT router | # Download [https://raw.githubusercontent.com/jonasluehrig/cghmn-get-connected/refs/heads/main/openwrt/setup-cghmn.sh this script from GitHub] to your OpenWRT router: <code>wget https://cghmn.snep.zip/connect.sh</code> | ||
# Run the following commands on the router: | # Run the following commands on the router: | ||
## <code>ash setup-cghmn.sh install-pkgs</code> | ## <code>ash setup-cghmn.sh install-pkgs</code> | ||
## <code>ash setup-cghmn.sh init</code> | ## <code>ash setup-cghmn.sh init</code> | ||
## You will be asked what network port you'd like to use for the Retro LAN. This is where you will plug in your retro machines to be part of the CGHMN. Choose a port that is not assigned to any OpenWRT interface like '''lan''' or '''wan''' or which not already part of a bridge and enter the Linux interface name, e.g. <code>eth1</code>, then press <code>[Enter]</code> to continue. If your router only has two ports and you're using one for WAN, then you first have to [https://openwrt.org/docs/guide-user/luci/luci.secure#allow_access_from_internet enable the web UI and SSH access via the '''wan''' OpenWRT interface], remove the entire '''lan''' OpenWRT interface to free the network port and continue the setup over the IP address your router got on its WAN side. If you only have a single Ethernet port, you're running on a router setup we can't really recommend, however you can configure VLANs and use a managed switch to both get a WAN DHCP address for internet access and have a separate VLAN for the Retro LAN bridge over a single port. This is commonly referred to as "[[wikipedia:Router_on_a_stick|router on a stick]]". Just enter the VLAN interface name here if you choose to go that route. | ## You will be asked what network port you'd like to use for the Retro LAN. This is where you will plug in your retro machines to be part of the CGHMN. Choose a port that is not assigned to any OpenWRT interface like '''lan''' or '''wan''' or which not already part of a bridge and enter the Linux interface name, e.g. <code>eth1</code>, then press <code>[Enter]</code> to continue. If your router only has two ports and you're using one for WAN, then you first have to [https://openwrt.org/docs/guide-user/luci/luci.secure#allow_access_from_internet enable the web UI and SSH access via the '''wan''' OpenWRT interface], remove the entire '''lan''' OpenWRT interface to free the network port and continue the setup over the IP address your router got on its WAN side. If you only have a single Ethernet port, you're running on a router setup we can't really recommend, however you can configure VLANs and use a managed switch to both get a WAN DHCP address for internet access and have a separate VLAN for the Retro LAN bridge over a single port. This is commonly referred to as "[[wikipedia:Router_on_a_stick|router on a stick]]". Just enter the VLAN interface name here if you choose to go that route. | ||
# Now you will be given some information on the console, including a Wireguard public key. Send one of the CGHMN admins (currently CursedSilicon and Snep) that key so we can add your router to our Wireguard server. | # Now you will be given some information on the console, including a Wireguard public key. Send one of the CGHMN admins (currently CursedSilicon and Snep) that key so we can add your router to our Wireguard server. If you cannot copy-paste, for example, because you're on a VM VNC console, you can run <code>ash setup-cghmn.sh pubkey-qr</code> to get a QR code printout of your public key, which can be scanned with a phone, tablet or software QR code parser to get the key as copy-pastable text. | ||
# In return, you will receive a tunnel IPv4 address (<code>100.89.128.x/32</code>) and a routed IPv4 subnet (<code>100.96.x.0/24</code>) from us. These will be needed on the third and final step of the setup script: | # In return, you will receive a tunnel IPv4 address (<code>100.89.128.x/32</code>) and a routed IPv4 subnet (<code>100.96.x.0/24</code>) from us. These will be needed on the third and final step of the setup script: | ||
## <code>ash setup-cghmn.sh set-tunnel-ip</code> | ## <code>ash setup-cghmn.sh set-tunnel-ip</code> | ||
# Once the script completed successfully, reboot the router to ensure all interfaces are up properly. After the reboot, your retro devices should receive an IP address in your routed IPv4 subnet on the Retro LAN port you chose above and be able to communicate with other machines on the CGHMN network. | # Once the script completed successfully, reboot the router to ensure all interfaces are up properly. After the reboot, your retro devices should receive an IP address in your routed IPv4 subnet on the Retro LAN port you chose above and be able to communicate with other machines on the CGHMN network. | ||
=== Get Connected - Manually (Linux, Wireguard only, GRETAP follows shortly) === | |||
In case you want to setup a connection into the network manually, here are the required steps and information you should be needing: | |||
* Generate a Wireguard private key and public key, this command writes a fresh Wireguard private key to <code>private-key</code> and the corresponsing public key to <code>public-key</code>: | |||
$ wg genkey | tee private-key | wg pubkey > public-key | |||
* NEVER share your private key, even with us! It should never be required outside of your own Wireguard setup! | |||
* You will, however, need to share your public key with us. Send CursedSilicon or Snep on the Discord or via IRC a message including the public key and we'll add you to the tunnel. | |||
* In return, you'll get two IP addresses from us: Your tunnel IP address, with which your router talks to our router, and a routed subnet, from which you can assign IPs to your own machines so they can talk to other CGHMN member devices on the network without NAT in the way. | |||
* Next, you'll need to fill a Wireguard configuration file with the two IP addresses, like below: | |||
[Interface] | |||
PrivateKey = <Your private key goes here> | |||
Address = <Your tunnel IP address goes here>/32 | |||
DNS = 100.89.128.0 | |||
MTU = 1420 | |||
[Peer] | |||
PublicKey = k/QiJIbMakMKgTCHVt8/D+8k4DzRVM6U33F3gMZfRUg= | |||
Endpoint = wg-admin.cursedsilicon.net:42070 | |||
AllowedIPs = 172.23.0.0/16, 100.89.128.0/22, 100.96.0.0/13 | |||
PersistentKeepalive = 15 | |||
* Save this file as <code>wg-cghmn.conf</code>, for example. | |||
* Then, run <code>wg-quick up ./wg-cghmn.conf</code>, perhaps requiring <code>doas</code>/<code>sudo</code>, to bring the tunnel up and connect to the network! | |||
This should bring whatever system you've set the tunnel up on onto the network and is now reachable for other members on the network, as long as the firewall on your device is congfigured accordingly, of course. | |||
<nowiki>#</nowiki>TODO: Add example of routed subnet configuration, perhaps on a different Wiki site | |||
=== Get connected - Server Side, the Admins Guide === | === Get connected - Server Side, the Admins Guide === | ||
| Line 54: | Line 85: | ||
# Navigate to VPN -> Wireguard -> Instances | # Navigate to VPN -> Wireguard -> Instances | ||
# Hit the "Apply" button | # Hit the "Apply" button | ||
# Do either one of these steps, depending on if you can SSH into the GRETAP endpoint container: | # Do '''either one''' '''(not both!)''' of these steps, depending on if you can SSH into the GRETAP endpoint container: | ||
## SSH into the CGHMN Proxmox Server and enter the command <code>pct enter 10403</code> | ## SSH into the CGHMN Proxmox Server and enter the command <code>pct enter 10403</code> | ||
## SSH directly into the GRETAP endpoint (formerly VXLAN endpoint) container with <code>ssh root@172.23.4.103</code> | ## SSH directly into the GRETAP endpoint (formerly VXLAN endpoint) container with <code>ssh root@172.23.4.103</code> | ||
# From there, run the following command: <code>bash /opt/vxlan-scripts/create-vxlan-interface.sh <member-tunnel-ip> <member-name></code> where you replace <code><member-tunnel-ip></code> with the IP tunnel address of the member as it was set above in the '''Address''' field, without the <code>/32</code> CIDR subnet mask, and replace the <code><member-name></code> with the same value you've entered above in the '''Name''' field. For example, like this: <code>bash /opt/vxlan-scripts/create-vxlan-interface.sh 100.89.128.6 member.snep.test</code> This will create a GRETAP (and for legacy purposes, a VXLAN) interface and bring them up automagically. ''Ignore the fact it still says "VXLAN" everywhere, it does both.'' | # From there, run the following command: <code>bash /opt/vxlan-scripts/create-vxlan-interface.sh <member-tunnel-ip> <member-name></code> where you replace <code><member-tunnel-ip></code> with the IP tunnel address of the member as it was set above in the '''Address''' field, without the <code>/32</code> CIDR subnet mask, and replace the <code><member-name></code> with the same value you've entered above in the '''Name''' field. For example, like this: <code>bash /opt/vxlan-scripts/create-vxlan-interface.sh 100.89.128.6 member.snep.test</code> This will create a GRETAP (and for legacy purposes, a VXLAN) interface and bring them up automagically. ''Ignore the fact it still says "VXLAN" everywhere, it does both.'' | ||
# Now you can send the member their Wireguard Tunnel IP and their routed subnet over and they can finish their client-side setup according to the mini-tutorial above. | # Now you can send the member their Wireguard Tunnel IP and their routed subnet over and they can finish their client-side setup according to the mini-tutorial above. | ||
# Rember to add the member and their tunnel and subnet IPs to the [[CGHMN-IP-Allocations|IP allocations page]] :) | |||
==== But wait, what even ''is'' their routed subnet? ==== | ==== But wait, what even ''is'' their routed subnet? ==== | ||
| Line 64: | Line 96: | ||
To get the routed subnet of a member, take the number from the last octet of the Wireguard tunnel IP of a member, say <code>100.89.128.'''6'''</code>, and put it into the third octet of the <code>100.96.0.0/13</code> IP block and replace the <code>/13</code> with <code>/24</code>, so you get <code>100.96.'''6'''.0/24</code>. That is their routed subnet, simple as that! | To get the routed subnet of a member, take the number from the last octet of the Wireguard tunnel IP of a member, say <code>100.89.128.'''6'''</code>, and put it into the third octet of the <code>100.96.0.0/13</code> IP block and replace the <code>/13</code> with <code>/24</code>, so you get <code>100.96.'''6'''.0/24</code>. That is their routed subnet, simple as that! | ||
=== After you get connected === | |||
There are a few optional things you might want to do. | |||
==== Network mailing list ==== | |||
There is a mailing list you can subscribe to if you want to be notified about things that may affect CGHMN or core services. You can subscribe to the list here: https://berwick-upon-tweed.cobaltqu.be/postorius/lists/cghmn-announce.lists.cobaltqu.be/. | |||
If you need to post to the list, you will need to subscribe before you can be added to the list of poster. | |||
==== Explore things available on the network ==== | |||
There is a collection of [[services people are running]] - things like email/hosting/chat/search/etc. | |||
Latest revision as of 22:36, 20 October 2025
This is a quick and dirty "how do I get on CGHMN"
Since the service is in "open beta" these steps are a bit vague and manual. But over time as we figure out what works we'll add more connection methods and better documentation
Step 1:
Let us know you'd like to connect!
(We'll need information from you such as your Wireguard Pubkey to let you connect to the network)

Hardware requirements
To connect your retro machine(s) to the CGHMN, you'll need the following:
- An Ethernet connection on your retro device(s) of choice, with a TCP/IP (v4) stack for now! TrumpetWinSock, Microsoft TCP/IP, whatever. It all works.
- Something with the ability to run Wireguard and forward IPv4 packets at the minimum and, for any non-IP packets,
gretapandnftables. Personally we recommend something running OpenWRT, like the GL-AR300M which we have successfully tested to work. We're currently working on a pre-built image for some select routers to make the setup easier for new members. A script to configure already existing OpenWRT instances can be found below. - Alternatively, you can also run the CGHMN routing on any standard Linux box which has at least one Ethernet port and either a second one or WiFi for internet connectivity.
A basic script to set up a Linux machine as a router is posted below(TODO!).
- Optionally: A simple network switch, in case you want to add multiple machines to the network. You plug one end into the CGHMN Router box and then your clients can all access CGHMN. Super easy!
On the right is an example of what a CGHMN router setup could look like.
Get connected - With OpenWRT
If you chose to go with an OpenWRT compatible router or want to run OpenWRT on typical x86 hardware/in a VM, you can follow these steps to get yourself connected to the CGHMN:
- Update your OpenWRT install to the latest version to ensure all required packages are available and compatible.
- Download this script from GitHub to your OpenWRT router:
wget https://cghmn.snep.zip/connect.sh - Run the following commands on the router:
ash setup-cghmn.sh install-pkgsash setup-cghmn.sh init- You will be asked what network port you'd like to use for the Retro LAN. This is where you will plug in your retro machines to be part of the CGHMN. Choose a port that is not assigned to any OpenWRT interface like lan or wan or which not already part of a bridge and enter the Linux interface name, e.g.
eth1, then press[Enter]to continue. If your router only has two ports and you're using one for WAN, then you first have to enable the web UI and SSH access via the wan OpenWRT interface, remove the entire lan OpenWRT interface to free the network port and continue the setup over the IP address your router got on its WAN side. If you only have a single Ethernet port, you're running on a router setup we can't really recommend, however you can configure VLANs and use a managed switch to both get a WAN DHCP address for internet access and have a separate VLAN for the Retro LAN bridge over a single port. This is commonly referred to as "router on a stick". Just enter the VLAN interface name here if you choose to go that route.
- Now you will be given some information on the console, including a Wireguard public key. Send one of the CGHMN admins (currently CursedSilicon and Snep) that key so we can add your router to our Wireguard server. If you cannot copy-paste, for example, because you're on a VM VNC console, you can run
ash setup-cghmn.sh pubkey-qrto get a QR code printout of your public key, which can be scanned with a phone, tablet or software QR code parser to get the key as copy-pastable text. - In return, you will receive a tunnel IPv4 address (
100.89.128.x/32) and a routed IPv4 subnet (100.96.x.0/24) from us. These will be needed on the third and final step of the setup script:ash setup-cghmn.sh set-tunnel-ip
- Once the script completed successfully, reboot the router to ensure all interfaces are up properly. After the reboot, your retro devices should receive an IP address in your routed IPv4 subnet on the Retro LAN port you chose above and be able to communicate with other machines on the CGHMN network.
Get Connected - Manually (Linux, Wireguard only, GRETAP follows shortly)
In case you want to setup a connection into the network manually, here are the required steps and information you should be needing:
- Generate a Wireguard private key and public key, this command writes a fresh Wireguard private key to
private-keyand the corresponsing public key topublic-key:
$ wg genkey | tee private-key | wg pubkey > public-key
- NEVER share your private key, even with us! It should never be required outside of your own Wireguard setup!
- You will, however, need to share your public key with us. Send CursedSilicon or Snep on the Discord or via IRC a message including the public key and we'll add you to the tunnel.
- In return, you'll get two IP addresses from us: Your tunnel IP address, with which your router talks to our router, and a routed subnet, from which you can assign IPs to your own machines so they can talk to other CGHMN member devices on the network without NAT in the way.
- Next, you'll need to fill a Wireguard configuration file with the two IP addresses, like below:
[Interface] PrivateKey = <Your private key goes here> Address = <Your tunnel IP address goes here>/32 DNS = 100.89.128.0 MTU = 1420 [Peer] PublicKey = k/QiJIbMakMKgTCHVt8/D+8k4DzRVM6U33F3gMZfRUg= Endpoint = wg-admin.cursedsilicon.net:42070 AllowedIPs = 172.23.0.0/16, 100.89.128.0/22, 100.96.0.0/13 PersistentKeepalive = 15
- Save this file as
wg-cghmn.conf, for example. - Then, run
wg-quick up ./wg-cghmn.conf, perhaps requiringdoas/sudo, to bring the tunnel up and connect to the network!
This should bring whatever system you've set the tunnel up on onto the network and is now reachable for other members on the network, as long as the firewall on your device is congfigured accordingly, of course.
#TODO: Add example of routed subnet configuration, perhaps on a different Wiki site
Get connected - Server Side, the Admins Guide
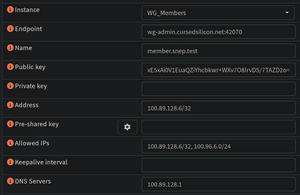
To get a member onto the network, they will send an admin of the project their randomly generated Wireguard key during the setup via the OpenWRT script. Here are the steps that admin will have to follow to get them up and running on the server side:
- Log in on the Core Router over an existing CGHMN network link
- Navigate to VPN -> Wireguard -> Peer Generator
- You will be asked to enter some data for the new peer, enter the following:
- Instance:
WG_Member - Endpoint:
wg-admin.cursedsilicon.net:42070 - Name:
member.<Nickname of the new member> - Public Key:
<their Wireguard public key they've sent over> - Private Key:
<blank> - Address:
<Next highest IP from 100.89.128.0/22, this is their tunnel IP and is auto-filled> - Pre-Shared Key:
<blank> - Allowed IPs:
<the same as Address>, <their routed subnet, see below> - Keepalive interval:
<blank> - DNS Servers:
<default value>
- Instance:
- Hit the "Store and generate next" button
- Navigate to VPN -> Wireguard -> Instances
- Hit the "Apply" button
- Do either one (not both!) of these steps, depending on if you can SSH into the GRETAP endpoint container:
- SSH into the CGHMN Proxmox Server and enter the command
pct enter 10403 - SSH directly into the GRETAP endpoint (formerly VXLAN endpoint) container with
ssh root@172.23.4.103
- SSH into the CGHMN Proxmox Server and enter the command
- From there, run the following command:
bash /opt/vxlan-scripts/create-vxlan-interface.sh <member-tunnel-ip> <member-name>where you replace<member-tunnel-ip>with the IP tunnel address of the member as it was set above in the Address field, without the/32CIDR subnet mask, and replace the<member-name>with the same value you've entered above in the Name field. For example, like this:bash /opt/vxlan-scripts/create-vxlan-interface.sh 100.89.128.6 member.snep.testThis will create a GRETAP (and for legacy purposes, a VXLAN) interface and bring them up automagically. Ignore the fact it still says "VXLAN" everywhere, it does both. - Now you can send the member their Wireguard Tunnel IP and their routed subnet over and they can finish their client-side setup according to the mini-tutorial above.
- Rember to add the member and their tunnel and subnet IPs to the IP allocations page :)
But wait, what even is their routed subnet?
Each members routed subnet comes per default from the 100.96.0.0/13 IPv4 block and has a /24 mask. This subnet is their "Retro LAN", to which all their retro computers are hooked into via the router of their choosing. By default, NAT is enabled on the routers, so it wouldn't make a difference which subnet is used on the remote end for the retro machines. However, if someone wants to host servers in the CGHMN and doesn't want to do port forwading, they can disable NAT and let other membres directly connect to their machines via this routed subnet.
To get the routed subnet of a member, take the number from the last octet of the Wireguard tunnel IP of a member, say 100.89.128.6, and put it into the third octet of the 100.96.0.0/13 IP block and replace the /13 with /24, so you get 100.96.6.0/24. That is their routed subnet, simple as that!
After you get connected
There are a few optional things you might want to do.
Network mailing list
There is a mailing list you can subscribe to if you want to be notified about things that may affect CGHMN or core services. You can subscribe to the list here: https://berwick-upon-tweed.cobaltqu.be/postorius/lists/cghmn-announce.lists.cobaltqu.be/.
If you need to post to the list, you will need to subscribe before you can be added to the list of poster.
Explore things available on the network
There is a collection of services people are running - things like email/hosting/chat/search/etc.